Reading-Notes
Code Fellows Python 401
Read: 33 - Authentication & Production Server
JSON Web Tokens
- JSON Web Token (JWT) defines a compact and self-contained way for securely transmitting JSON information
when to use:
- Authorization
- Info Exchange
JWT Structure
- Header
- Payload
- Signature
Header
two parts: the type of the token, and the signing algorithm
{
"alg": "HS256",
"typ": "JWT"
}
Payload
- contains the claims
- statements about an entity and additional data
claims:
- statements about an entity and additional data
- Registered claims: predefined claims which are not mandatory but recommended
- Public claims: can be defined at will by those using JWTs but should be defined as a URI that contains a collision resistant namespace
- Private claims: custom claims created to share information
ex.
{
"sub": "1234567890",
"name": "John Doe",
"admin": true
}
Signature
To create the signature part you have to take the encoded header, the encoded payload, a secret, the algorithm specified in the header, and sign that.
ex
HMACSHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),
secret)
Use diagram
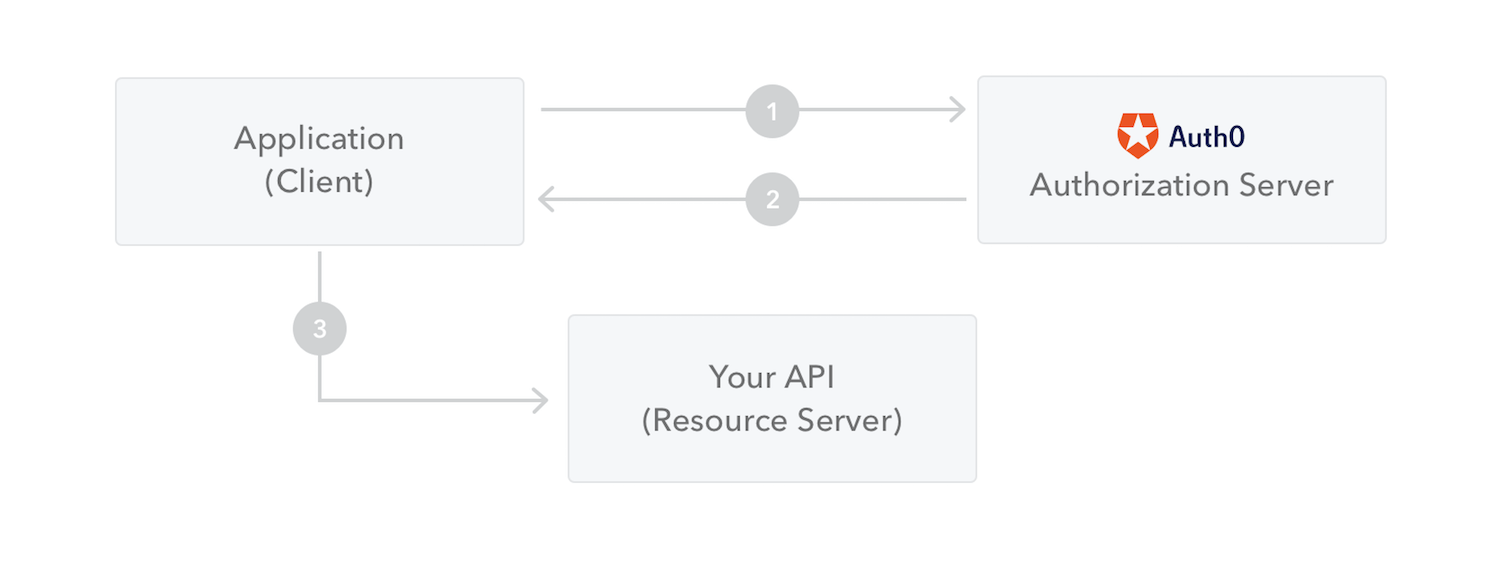
Why use them
- less verbose
- compact
DRF JWT Authentication
https://build.vsupalov.com/django-runserver-in-production/
- server started with runserver is not guaranteed to be performant
- only use tech in production
- DJANGO provides a uwsgi.py
- use a production-ready web server like Nginx
- let your app be handled by a WSGI application server like Gunicorn.
- with Heroku, a web server is provided implicitly